In recent years, second-generation identity card readers have been widely used to cover government, finance, securities,*, transportation, petrochemical, social security, education, taxation, power, corporate office automation, entertainment and consumer sectors and industries. It adopts the internationally advanced TypeB non-contact IC card reading technology, together with a special ID security control module (SAM) authorized by the Ministry of Security, and conducts security authentication with special chips within the second generation resident ID card through wireless transmission. The personal information in the chip is read out, this information is uploaded to the computer, and functions such as decoding, display, storage, inquiry, and automatic entry are completed.
The second-generation ID card reader is a device capable of judging whether an ID card is falsified. Like a money detector, it can effectively identify the authenticity of an ID card. The second-generation ID card contains an RFID chip, and the second-generation ID card reads a card. The information stored in the device, ID card, including names, addresses, photos and other information will be displayed one by one. The second generation chip adopts smart card technology, the chip can not be copied, high security, with the second generation ID card reader, false identity The card will have no place to hide. The second generation resident ID card can be read and inquired to verify the authenticity of the second generation resident ID card.
Starting from September 1, 2013, the "Regulations on Registration of Real User Information of Telephone Users" formulated by the Ministry of Industry and Information Technology requires that telephone users must access real identity information when they access the Internet.
The paperless/real-name system is not only a national legal requirement, but also an important basis for operation and management of major operations and improvement of customer quality.
However, the existing ID card identifiers are stand-alone devices, which result in huge purchase costs; long lead times; therefore, they are not suitable for large-scale unified procurement; in particular, the upgrade costs in the later period are even greater (2013 has already enabled three generations ID card, equivalent to a few years later, now all ID recognizers need to be repurchased). In addition, there are many computers and business systems that are not in the operator's terminal terminals. After the SAM module is deployed on the cloud server, the client reads the second-generation card content information and hands it over to the cloud security module for parsing. The parsed result is then returned to the client to complete the second-generation resident ID card reading and verification work. After nearly 3 months of R&D and testing, the non-contact smart card reader independently developed by our company is equipped with the functions of reading and writing common contactless smart cards based on IOS1443typeA and B protocols, NFC electronic tags, and mobile NFC chips. The outside also realized the reading function of the content of second-generation resident ID cards. This greatly reduces the purchase cost of the ID card reader, shortens the procurement cycle, and increases the market penetration rate.
The identity of each ID card is authentic and the data is decoded. The entire process is a mutual authentication process. There are more than 40 data handshake processes. The protocols used in these processes are the cryptographic protocols of the SAM module, which cannot be decrypted. The result is decoded by the server of the decoding server through the dll provided by the department. At the same time, the authentication file of the SAM module is required; otherwise, it cannot be decoded; the decoded data can be sent to the designated destination according to the requirements of the mobile company and transmitted to the reader terminal by default. The computer/phone.
1. Theoretical Basis Current readers of the ID card in the market include a security encryption module in each reader. Because of the long delivery time and high price of the security encryption module (SAM module), it is not suitable for mobile companies (or other department systems that require bulk purchases) to purchase equipment on a large scale.
This solution effectively solves the above problem: The design concept of this solution is to connect multiple service terminals to a secure encryption module (SAM module) through the Internet, and realize the function of multiple service terminals sharing a secure encryption module.
2. Economic analysis 1) The purchase cost is cheap: Because only the decoding device is installed on the decoding server, each peripheral terminal only needs to install the card reading device, so the cost is greatly reduced. Can reduce costs by 90%.
Calculated by Guangdong Mobile with 40,000 purchases, it can save more than 30 million purchase costs. If it is promoted to the whole country, it will gain greater economic benefits.
2) Low upgrade costs: In the future, the Department will promote third-generation ID cards, and existing second-generation card readers will definitely need to re-purchase the latest ID card readers in the future, causing great waste. Because the decoders are all on the server, the readers of each counter do not need to be replaced. It is only necessary to replace or upgrade the decoder on the server. Can reduce costs by 90%.
3. Extensiveness analysis 1) The realization of omni-channel coverage for computer-free, system-free peripheral terminals, only through the mobile phone connection can achieve identity card identification, reading. Greatly reduce the implementation difficulty of real-name system omni-channel coverage.
2) It is easy to use, plug and play only needs to install decoding equipment on the server of the operator company intranet to serve the province, which is convenient for the provincial company to manage the company. For customer service personnel at the terminal, simply connect the reading device to the mobile phone. Therefore, the implementation of the promotion is very difficult, equivalent to stand-alone ID card reader.
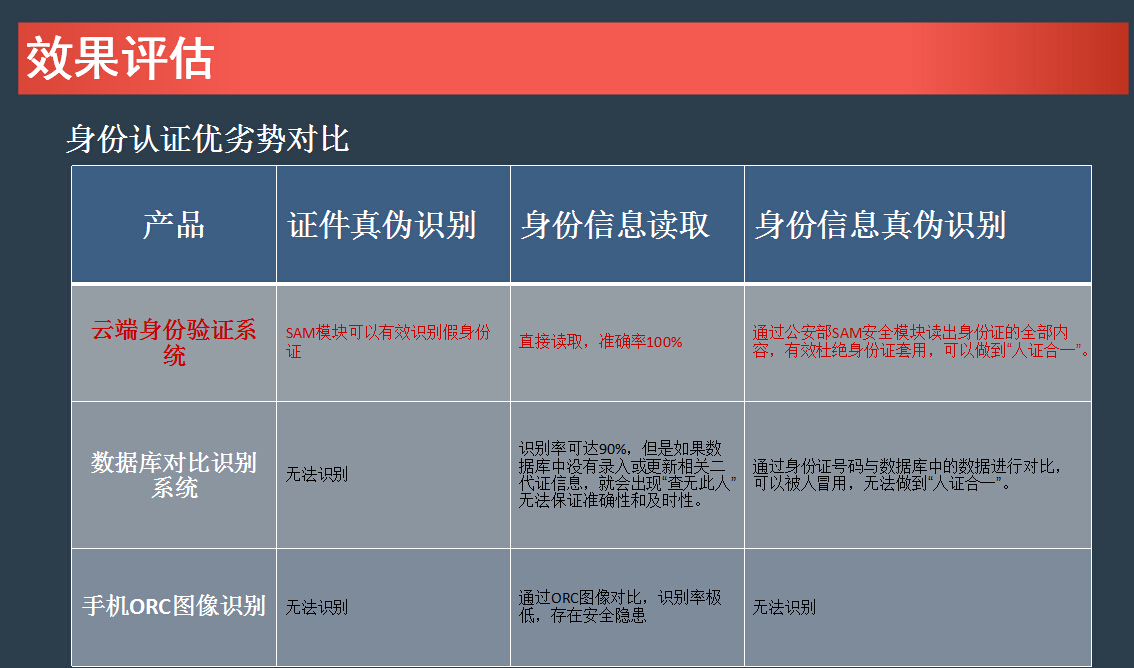
4. Security Analysis The past “online database comparison and recognition†and the use of OCR technology to obtain information through mobile phone photo ID cards have huge loopholes: the identity information cannot identify the authenticity, and the ID card itself cannot be authentic; for fake ID cards, "Double ID card" only through the * sam decoding module, can be truly recognized.
Any most accurate and effective ID reading/recognition device (scheme) must have no *secure cryptographic module (SAM module) authorized by the Ministry; the authenticity of each ID card, data decoding, and the entire process is a mutual authentication process. Among them, there are more than 40 data handshaking processes. The protocols used by these processes are the cryptographic protocols of the SAM module, which cannot be decrypted. The data results are decoded by the decoding server's device through the DLL provided by the department, and the SAM module is required. The authentication file, otherwise it can not be decoded; the decoded data can be sent to the designated destination according to the requirements, and it is transmitted to the computer/phone of the card reader terminal by default.
5. Product Architecture Design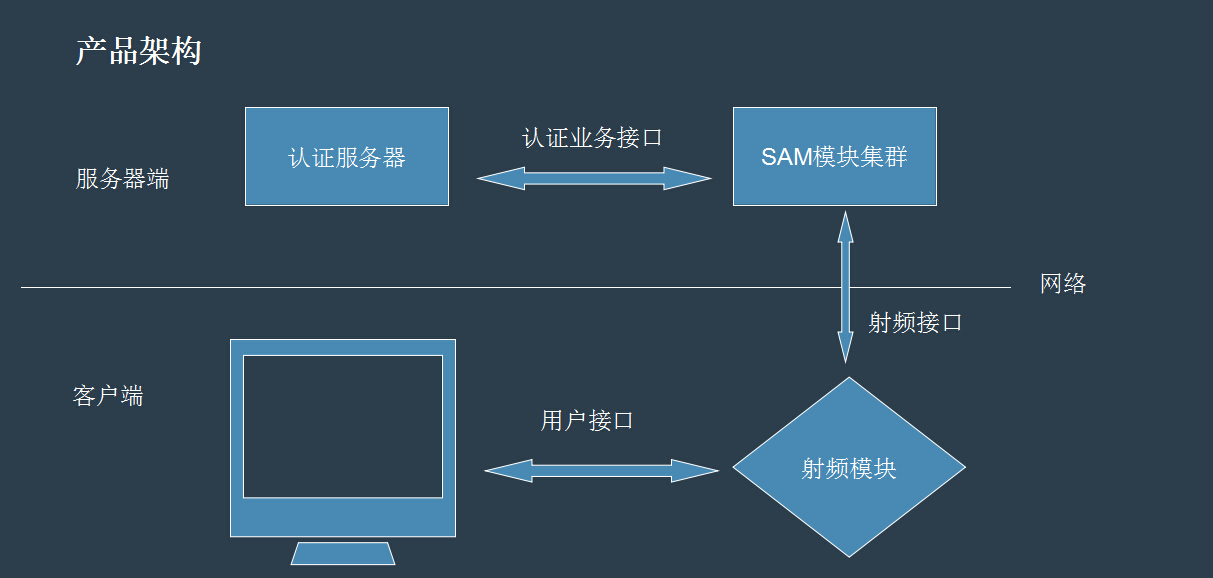
Network ID verification system architecture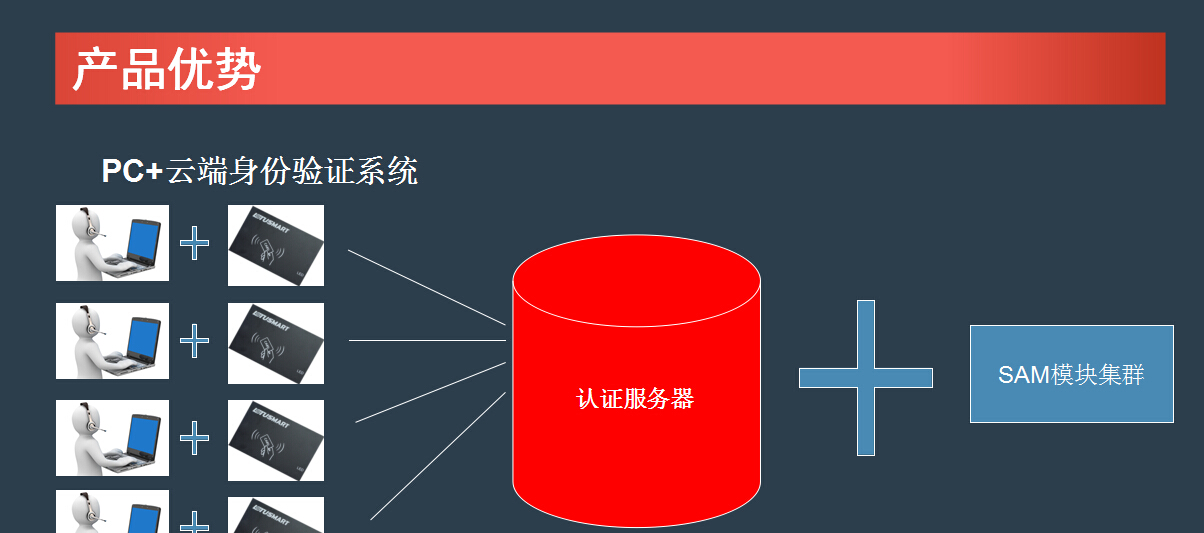
The online version of the ID card reader is compared with a traditional ID card reading ID reader.
The second-generation ID card reader is a device capable of judging whether an ID card is falsified. Like a money detector, it can effectively identify the authenticity of an ID card. The second-generation ID card contains an RFID chip, and the second-generation ID card reads a card. The information stored in the device, ID card, including names, addresses, photos and other information will be displayed one by one. The second generation chip adopts smart card technology, the chip can not be copied, high security, with the second generation ID card reader, false identity The card will have no place to hide. The second generation resident ID card can be read and inquired to verify the authenticity of the second generation resident ID card.
Starting from September 1, 2013, the "Regulations on Registration of Real User Information of Telephone Users" formulated by the Ministry of Industry and Information Technology requires that telephone users must access real identity information when they access the Internet.
The paperless/real-name system is not only a national legal requirement, but also an important basis for operation and management of major operations and improvement of customer quality.
However, the existing ID card identifiers are stand-alone devices, which result in huge purchase costs; long lead times; therefore, they are not suitable for large-scale unified procurement; in particular, the upgrade costs in the later period are even greater (2013 has already enabled three generations ID card, equivalent to a few years later, now all ID recognizers need to be repurchased). In addition, there are many computers and business systems that are not in the operator's terminal terminals. After the SAM module is deployed on the cloud server, the client reads the second-generation card content information and hands it over to the cloud security module for parsing. The parsed result is then returned to the client to complete the second-generation resident ID card reading and verification work. After nearly 3 months of R&D and testing, the non-contact smart card reader independently developed by our company is equipped with the functions of reading and writing common contactless smart cards based on IOS1443typeA and B protocols, NFC electronic tags, and mobile NFC chips. The outside also realized the reading function of the content of second-generation resident ID cards. This greatly reduces the purchase cost of the ID card reader, shortens the procurement cycle, and increases the market penetration rate.
The identity of each ID card is authentic and the data is decoded. The entire process is a mutual authentication process. There are more than 40 data handshake processes. The protocols used in these processes are the cryptographic protocols of the SAM module, which cannot be decrypted. The result is decoded by the server of the decoding server through the dll provided by the department. At the same time, the authentication file of the SAM module is required; otherwise, it cannot be decoded; the decoded data can be sent to the designated destination according to the requirements of the mobile company and transmitted to the reader terminal by default. The computer/phone.
1. Theoretical Basis Current readers of the ID card in the market include a security encryption module in each reader. Because of the long delivery time and high price of the security encryption module (SAM module), it is not suitable for mobile companies (or other department systems that require bulk purchases) to purchase equipment on a large scale.
This solution effectively solves the above problem: The design concept of this solution is to connect multiple service terminals to a secure encryption module (SAM module) through the Internet, and realize the function of multiple service terminals sharing a secure encryption module.
2. Economic analysis 1) The purchase cost is cheap: Because only the decoding device is installed on the decoding server, each peripheral terminal only needs to install the card reading device, so the cost is greatly reduced. Can reduce costs by 90%.
Calculated by Guangdong Mobile with 40,000 purchases, it can save more than 30 million purchase costs. If it is promoted to the whole country, it will gain greater economic benefits.
2) Low upgrade costs: In the future, the Department will promote third-generation ID cards, and existing second-generation card readers will definitely need to re-purchase the latest ID card readers in the future, causing great waste. Because the decoders are all on the server, the readers of each counter do not need to be replaced. It is only necessary to replace or upgrade the decoder on the server. Can reduce costs by 90%.
3. Extensiveness analysis 1) The realization of omni-channel coverage for computer-free, system-free peripheral terminals, only through the mobile phone connection can achieve identity card identification, reading. Greatly reduce the implementation difficulty of real-name system omni-channel coverage.
2) It is easy to use, plug and play only needs to install decoding equipment on the server of the operator company intranet to serve the province, which is convenient for the provincial company to manage the company. For customer service personnel at the terminal, simply connect the reading device to the mobile phone. Therefore, the implementation of the promotion is very difficult, equivalent to stand-alone ID card reader.
4. Security Analysis The past “online database comparison and recognition†and the use of OCR technology to obtain information through mobile phone photo ID cards have huge loopholes: the identity information cannot identify the authenticity, and the ID card itself cannot be authentic; for fake ID cards, "Double ID card" only through the * sam decoding module, can be truly recognized.
Any most accurate and effective ID reading/recognition device (scheme) must have no *secure cryptographic module (SAM module) authorized by the Ministry; the authenticity of each ID card, data decoding, and the entire process is a mutual authentication process. Among them, there are more than 40 data handshaking processes. The protocols used by these processes are the cryptographic protocols of the SAM module, which cannot be decrypted. The data results are decoded by the decoding server's device through the DLL provided by the department, and the SAM module is required. The authentication file, otherwise it can not be decoded; the decoded data can be sent to the designated destination according to the requirements, and it is transmitted to the computer/phone of the card reader terminal by default.
5. Product Architecture Design

Network ID verification system architecture

The online version of the ID card reader is compared with a traditional ID card reading ID reader.

Industrial Door System ,Hanging Door Roller,Hanger Roller Bracket,Hanging Roller Track Bracket
Jiaxing Gates Hardware Products Co.,Ltd , https://www.888gates.com